Do you scan for Log4j? - Yes, we do! Here's how you can check for Log4Shell in 3 easy ways.
We have added detection capabilities for CVE-2021-44228 (Log4Shell) within our tools. These scanners implement distinct detection techniques.
Log4Shell detection using the Website Scanner
We recommend using the Website Scanner as the primary detection tool for Log4Shell - either using the Deep Scan configuration or just the dedicated Log4j test.
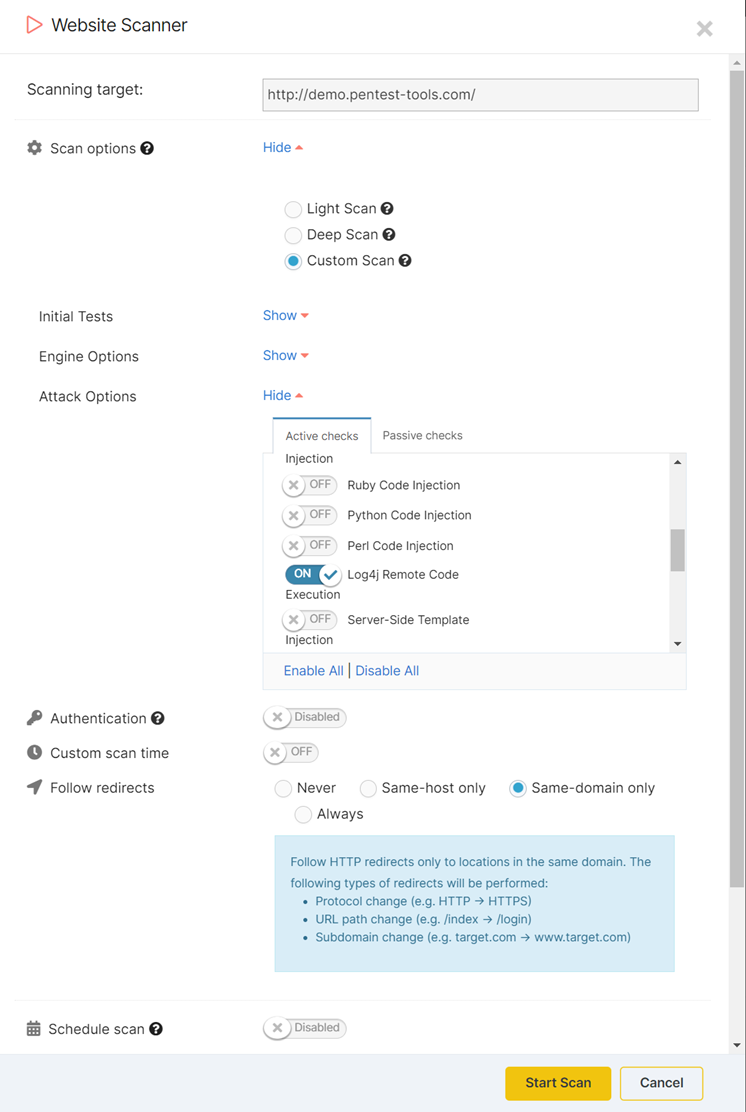
The Website Scanner performs crawling of the target application and indexes all the injection points, so it has extensive coverage of the target application, therefore we believe it is the most effective detection method for Log4Shell.
Log4Shell detection using the Network Scanner
The custom detection modules we are implementing in the Network Scanner have a different approach to detecting Log4Shell. Instead of looking at the target as a generic web application, the Network Scanner searches for the vulnerability in specific or well-known applications that are using Log4j.
We implemented this detection with the Network Scanner by using Sniper Automatic Exploiter modules, which will soon have the additional capability to exploit the vulnerability when the user also wants to prove that the risk is real.
You will be able to perform exploitation exclusively with Sniper, which is coming soon to the Pentest-Tools.com platform.
🤖 Log4Shell detection using our dedicated Log4Shell Pentest Robot
To help you identify potential issues faster, we’ve created a ready-to-use pentest robot that scans for Log4Shell exclusively using our Website Scanner – with a predefined set of options.
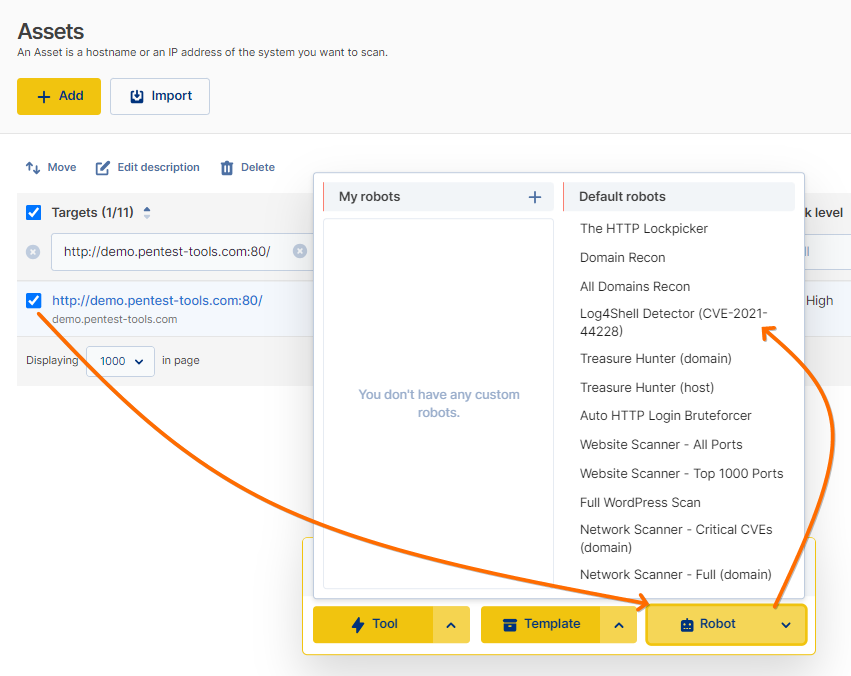
This will perform a quick TCP Port Scan for the target and run a Website Scanner for any web services discovered. Furthermore, using this specialized robot helps both other pen-testers and us by decreasing the load that Deep Scans create.
Check out the full guide and more pro tips in our learning center right here!
